Information Security
Information Security Program
Last modified 10/14/2020
Overview and Purpose
It is the mission of the Illinois State University Information Security Office (ISO) to (i) support the missions, goals, and objectives of the University, (ii) reduce the risk posed to the University due to loss, disruption, or corruption of information and information systems, and (iii) assure that the University is in compliance with applicable state, federal, and industry laws, rules, and regulations related to information security.
This document describes the institution-wide information security program that implements, controls, and maintains the functions, procedures, and standards supported or managed by the ISO in its mission.
Framework
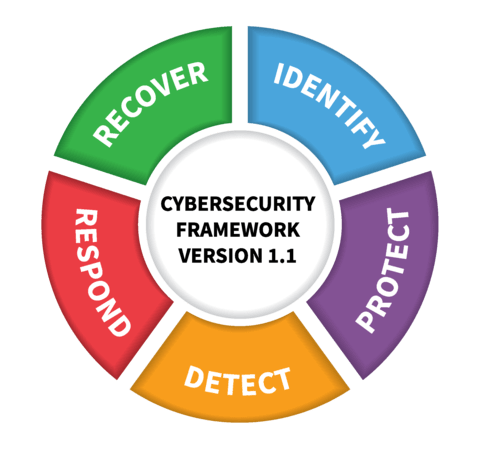
To ensure that the information security program is efficient and effective, the University has chosen to align with the standards and frameworks published by the Information Technology Laboratory (ITL) of the National Institute of Standards and Technology (NIST). Most notable is the NIST Cyber Security Framework (CSF) that this program is modeled after.
- NIST Cyber Security Framework
The NIST Cyber Security Framework (CSF) integrates industry standards and best practices to help organizations manage their cybersecurity risks. It provides a common language that allows staff at all levels within an organization—and at all points in a supply chain—to develop a shared understanding of their cybersecurity risks.
The Framework not only helps organizations understand their cybersecurity risks (threats, vulnerabilities and impacts), but how to reduce these risks with customized measures. The Framework also helps them respond to and recover from cybersecurity incidents, prompting them to analyze root causes and consider how they can make improvements.
Source: https://www.nist.gov/industry-impacts/cybersecurity-framework
Functions
The following functions of the information security program are in direct alignment with the NIST CSF. The activity categories managed by these functions are included in each section. Given the breadth and depth of these functions, many of them will operate in conjunction with each other.
- Identify
Develop an organizational understanding to manage cybersecurity risk to systems, people, assets, data, and capabilities.
Asset Management
The data, personnel, devices, systems, and facilities that enable the organization to achieve business purposes are identified and managed consistent with their relative importance to business objectives and the organization’s risk strategy.
Business Environment
The organization’s mission, objectives, stakeholders, and activities are understood and prioritized; this information is used to inform cybersecurity roles, responsibilities, and risk management decisions.
Governance
The policies, procedures, and processes to manage and monitor the organization’s regulatory, legal, risk, environmental, and operational requirements are understood and inform the management of cybersecurity risk.
Risk Assessment
The organization understands the cybersecurity risk to organizational operations (including mission, functions, image, or reputation), organizational assets, and individuals.
Risk Management Strategy
The organization’s priorities, constraints, risk tolerances, and assumptions are established and used to support operational risk decisions.
Supply Chain Risk Management
The organization’s priorities, constraints, risk tolerances, and assumptions are established and used to support risk decisions associated with managing supply chain risk. The organization has established and implemented the processes to identify, assess and manage supply chain risks.
- Protect
Develop and implement appropriate safeguards to ensure delivery of critical services.
Identity Management and Access Control
Access to physical and logical assets and associated facilities is limited to authorized users, processes, and devices, and is managed consistent with the assessed risk of unauthorized access to authorized activities and transactions. Includes authentication mechanisms.
Awareness and Training
The organization’s personnel and partners are provided cybersecurity awareness education and are trained to perform their cybersecurity-related duties and responsibilities consistent with related policies, procedures, and agreements.
Data Security
Information and records (data) are managed consistent with the organization’s risk strategy to protect the confidentiality, integrity, and availability of information.
Information Protection Processes and Procedures
Security policies (that address purpose, scope, roles, responsibilities, management commitment, and coordination among organizational entities), processes, and procedures are maintained and used to manage protection of information systems and assets.
Maintenance
Maintenance and repairs of industrial control and information system components are performed consistent with policies and procedures.
Protective Technology
Technical security solutions are managed to ensure the security and resilience of systems and assets, consistent with related policies, procedures, and agreements.
- Detect
Develop and implement appropriate activities to identify the occurrence of a cybersecurity event.
Anomalies and Event
Anomalous activity is detected and the potential impact of events is understood.
Security Continuous Monitoring
The information system and assets are monitored to identify cybersecurity events and verify the effectiveness of protective measures.
Detection Processes
Detection processes and procedures are maintained and tested to ensure awareness of anomalous events.
- Respond
Develop and implement appropriate activities to take action regarding a detected cybersecurity incident.
Response Planning
Response processes and procedures are executed and maintained, to ensure response to detected cybersecurity incidents.
Communications
Response activities are coordinated with internal and external stakeholders (e.g. external support from law enforcement agencies).
Analysis
Analysis is conducted to ensure effective response and support recovery activities.
Mitigation
Activities are performed to prevent expansion of an event, mitigate its effects, and resolve the incident.
Improvements
Organizational response activities are improved by incorporating lessons learned from current and previous detection/response activities.
- Recover
Develop and implement appropriate activities to maintain plans for resilience and to restore any capabilities or services that were impaired due to a cybersecurity incident.
Recovery Planning
Recovery processes and procedures are executed and maintained to ensure restoration of systems or assets affected by cybersecurity incidents.
Improvements
Recovery planning and processes are improved by incorporating lessons learned into future activities.
Communications
Restoration activities are coordinated with internal and external parties (e.g. coordinating centers, Internet Service Providers, owners of attacking systems, victims, other CSIRTs, and vendors).
Key Roles and Responsibilities
Information security is a shared responsibility that must be integrated into all aspects of the University administrative and academic operations. This section focuses on the specific roles and responsibilities involved in securing information and supporting the information security program.
- Chief Information Security Officer
The Chief Information Security Officer (CISO) is the designated individual responsible for the coordination of the information security program. They are also responsible for the development, implementation, and maintenance of the program components.
- Information Security Staff
The information security staff of the University are responsible for promoting awareness of this program and its underlying functions, procedures, and standards. They are also responsible for direct action within various activities of the information security program.
- IT Staff
The IT staff of the University are responsible for operating in accordance with this program for the systems and data they directly support, maintain, and manage.
Applicable Laws, Rules, and Regulations
This policy seeks to ensure compliance with applicable state and federal laws, rules, and regulations.
- Applicable Laws, Rules, and Regulations
The following is a non-exhaustive list of applicable laws, rules, and regulations used to inform the creation of this policy:
- Illinois Freedom of Information Act (5 ILCS 140)
- Illinois Identity Protection Act (5 ILCS 179)
- Illinois Personal Information Protection Act (815 ILCS 530)
- The Family Educational Rights and Privacy Act (FERPA) (20 U.S.C. § 1232g; 34 CFR Part 99)
- Federal Bureau of Investigations Criminal Justice Information Services (CJIS) Security Policy
- Federal Information Processing Standard (FIPS) 199, Standards for Security Categorization of Federal
Information and Information Systems - Federal Information Processing Standard (FIPS) 200, Minimum Security Requirements for Federal
Information and Information Systems - Federal Internal Revenue Service (IRS) Publication 1075 Tax Information Security Guidelines for
Federal, State and Local Agencies - Federal Information Security Modernization Act of 2014, which amends the Federal Information
Security Management Act of 2002 (FISMA) - Freedom of Information Act (FOIA), 5 U.S.C. § 552, as amended by Public Law No.104-231, 110 Stat.
3048, Electronic Freedom of Information Act - Gramm-Leach-Bliley Act (GLB Act or GLBA), also known as the Financial Modernization Act of 1999
In accordance with the Safeguards Rule of the Gramm-Leach Bliley Act (GLBA), the University must develop, implement, and maintain an information security program.
As defined under GLBA, an information security program is the administrative, technical, and physical safeguards in place to access, collect, distribute, process, protect, store, use, transmit, dispose of, or otherwise handle customer (student) information.
- Health Insurance Portability and Accountability Act (P.L. 104-191)
- National Institute of Standards and Technology (NIST) Special Publication 800-53 Security and Privacy Controls for Federal Information Systems and Organizations
- Payment Card Industry (PCI) Data Security Standard (DSS)
- Privacy Act of 1974 (P.L. 93-579)
- State Officials and Employees Ethics Act (5 ILCS 430)
Glossary
To assist in the awareness and understanding of key terms used within the information security program, the following glossary has been compiled for reference using the same language provided in the NIST CSF specification.
| Term | Definition |
|---|---|
| Critical Infrastructure | Systems and assets, whether physical or virtual, so vital to the United States that the incapacity or destruction of such systems and assets would have a debilitating impact on cybersecurity, national economic security, national public health or safety, or any combination of those matters. |
| Cybersecurity | The process of protecting information by preventing, detecting, and responding to attacks |
| Cybersecurity Event | A cybersecurity change that may have an impact on organizational operations (including mission, capabilities, or reputation). |
| Cybersecurity Incident | A cybersecurity event that has been determined to have an impact on the organization prompting the need for response and recovery. |
| Privileged User | A user that is authorized (and, therefore, trusted) to perform security-relevant functions that ordinary users are not authorized to perform. |
| Risk | A measure of the extent to which an entity is threatened by a potential circumstance or event, and typically a function of: (i) the adverse impacts that would arise if the circumstance or event occurs; and (ii) the likelihood of occurrence. |
| Supplier | Product and service providers used for an organization’s internal purposes (e.g., IT infrastructure) or integrated into the products of services provided to that organization’s users. |