Endpoint Management
Getting Started with Windows LAPS
Last modified 5/9/2023
Overview
Windows LAPS (Local Administrator Password Solution) is a free solution by Microsoft that provides a secure way to manage local administrator passwords on Windows computers.
Traditionally, local administrator passwords are set and managed manually, which can lead to poor password hygiene, such as reusing passwords, and can leave computers vulnerable to attacks. LAPS addresses these issues by automatically setting unique, complex passwords for the local administrator account on each computer, and storing these passwords in Active Directory (AD) or Azure Active Directory (AAD) where they can be retrieved by authorized users. Optionally, these passwords can also be encrypted for even further protection.
You can find more information about Windows LAPS at the following locations:
- Overview: https://learn.microsoft.com/en-us/windows-server/identity/laps/laps-overview
- PowerShell Cmdlet Reference: https://learn.microsoft.com/en-us/powershell/module/laps/
Setting Up Windows LAPS
OS Compatibility
Windows LAPS is available on the following operating systems with the April 11, 2023 update or later installed:
- Windows 11
- Windows 10
- Windows Server 2022
- Windows Server 2019
User Permissions to LAPS Attributes
Before You Begin
Legacy LAPS uses the ExtendedRightHolder AD permission to view the protected LAPS attributes. This will continue to work for Windows LAPS, but is not recommended going forward and may stop functioning correctly in the future. If you use Legacy LAPS today, your team has most likely already performed this or had CCA grant it on your OUs.
Microsoft has additional guidence for its removal found, which can be found here: https://learn.microsoft.com/en-us/windows-server/identity/laps/laps-scenarios-windows-server-active-directory#remove-extended-rights-permissions
Configuring new Windows LAPS Permissions
You can setup user/group permissions to Windows LAPS following the sections below:
- Read Password Permission
You can specify who can read various password attributes by using the Set-LapsADReadPasswordPermission cmdlet.
To add the permission to a group, perform the following :
- Login to a LAPS compatible endpoint or server with the Aprill 11, 2023 update using an account that has permissions to modify your OUs.
- Run the following Powershell command:
Set-LapsADReadPasswordPermission -Identity 'ENTER_DISTINGUISHED_NAME_HERE' -AllowedPrincipals @("ADILSTU\ENTER_GROUP_NAME_HERE_1", "ADILSTU\ENTER_MORE_GROUPS_WITH_COMMAS")
Cmdlet Reference: https://learn.microsoft.com/en-us/powershell/module/laps/set-lapsadreadpasswordpermission
- Reset Password Permission
You can specify who can read and set the password expiration time attribute by using the Set-LapsADResetPasswordPermission cmdlet.
To add the permission to a group, perform the following :
- Login to a LAPS compatible endpoint or server with the Aprill 11, 2023 update using an account that has permissions to modify your OUs.
- Run the following Powershell command:
Set-LapsADResetPasswordPermission -Identity 'ENTER_DISTINGUISHED_NAME_HERE' -AllowedPrincipals @("ADILSTU\ENTER_GROUP_NAME_HERE_1", "ADILSTU\ENTER_MORE_GROUPS_WITH_COMMAS")
Cmdlet Reference: https://learn.microsoft.com/en-us/powershell/module/laps/set-lapsadresetpasswordpermission
Computer SELF Permissions
In the OUs where Windows LAPS will be implemented, Computer objects will need to have the SELF permission updated in those OUs.
In order to do this, perform the following:
- Login to a LAPS compatible endpoint or server with the Aprill 11, 2023 update using an account that has permissions to modify your OUs.
- Run the following Powershell command:
Set-LapsADComputerSelfPermission -Identity 'ENTER_DISTINGUISHED_NAME_HERE'
LAPS Settings Deployment
To enable Windows LAPS, you will need to deploy new Group Policy settings specifically for Windows LAPS.
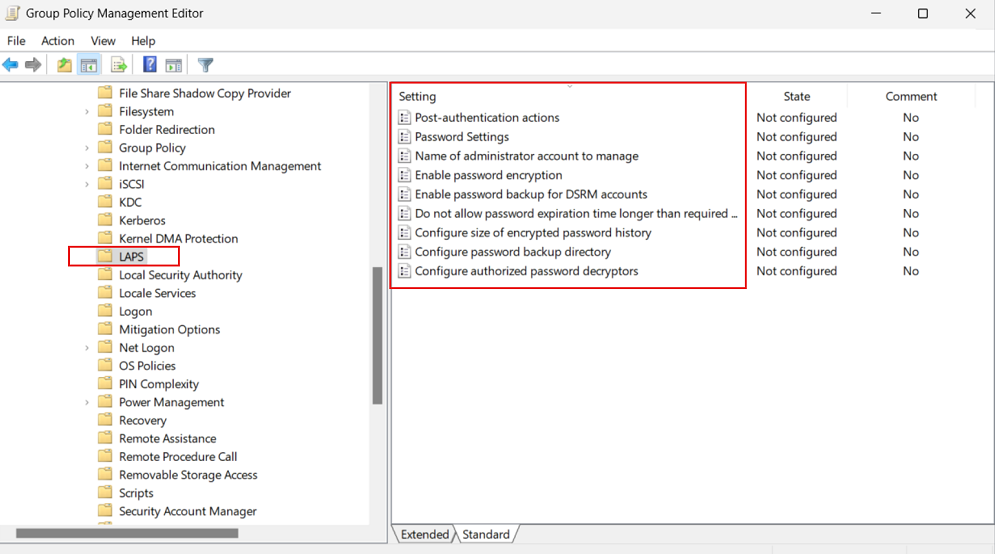
To access the Windows LAPS Group Policy settings, use on a device that has RSAT installed and is a LAPS compatible endpoint or server with the Aprill 11, 2023 update. Open Group Policy Management Editor, go to Computer Configuration > Administrative Templates > System > LAPS, to access the new settings.
FAQs
- I'm not ready to move to Windows LAPS yet, and I have Legacy LAPS deployed. What do I need to do?
Nothing. Legacy LAPS will continue to work as normal. You must deploy Windows LAPS settings to enable Windows LAPS.
- If I have both Windows LAPS and Legacy LAPS settings deployed at the same time. What happens?
From Microsoft Docs:
"Windows LAPS queries all known registry key policy roots, starting at the top and moving down. If no settings are found under a root, that root is skipped and the query proceeds to the next root. When a root that has at least one explicitly defined setting is found, that root is used as the active policy. If the chosen root is missing any settings, the settings are assigned their default values."
| Policy name | Policy registry key root |
|---|---|
| LAPS CSP (Intune) | HKLM\Software\Microsoft\Policies\LAPS |
| LAPS Group Policy | HKLM\Software\Microsoft\Windows\CurrentVersion\Policies\LAPS |
| LAPS Local Configuration | HKLM\Software\Microsoft\Windows\CurrentVersion\LAPS\Config |
| Legacy Microsoft LAPS | HKLM\Software\Policies\Microsoft Services\AdmPwd |
Feedback
To suggest an update to this article, ISU students, faculty, and staff should submit an Update Knowledge/Help Article request and all others should use the Get IT Help form.